ISO/IEC gives guidelines for organizational information security standards and information security management practices including the selection, implementation and management of controls taking into consideration the organization's information security risk environment(s). It is designed to be used by organizations that intend to. Assemble an implementation team. Your first task is to appoint a project leader to oversee the. The main goal of ISO 27002 is to establish guidelines and general principles for starting, implementing, maintaining and improving the management of information security in an organization. This also includes selection, implementation and management of controls, taking into account the risk environments found in the company.
Several people have asked for an IT Audit Program Template for an audit based on the ISO/IEC 27002:2005(E) security standard. This template, which can be found here
[download]
will help you in your assessment of an organization’s information security program for CobiT Maturity Level 4.
CobiT Maturity Level 4 Managed and Measurable, states that the status of the Internal Control Environment is “There is an effective internal control and risk management environment. A formal, documented evaluation of controls occurs frequently. Many controls are automated and regularly reviewed. Management is likely to detect most control issues, but not all issues are routinely identified. There is consistent follow-up to address identified control weaknesses. A limited, tactical use of technology is applied to automate controls.”
- ISO 27002 Information Security Guidelines Checklist Use this ISO 27002 information security guidelines checklist to ensure that your ISMS security controls adhere to the ISO 27001 information security standard. ISO 27002 provides an overview list of best practices for implementing the ISO.
- Plain English ISO IEC 27002 Checklist. ISO IEC is a comprehensive information security standard. Use it to protect and preserve the confidentiality, integrity, and availability of information. ISO IEC Information Security Checklist.
Iso 27002 Document Checklist
CobiT Maturity Level 4 Managed and Measurable, states that for the Establishment of Internal Controls; “IT process criticality is regularly defined with full support and agreement from the relevant business process owners. Assessment of control requirements is based on policy and the actual maturity of these processes, following a thorough and measured analysis involving key stakeholders. Accountability for these assessments is clear and enforced. Improvement strategies are supported by business cases. Performance in achieving the desired outcomes is consistently monitored. External control reviews are organized occasionally.”

As an example, one of the questions in the section on “Allocation of information security responsibilities” is written as follows:
Are the assets and security processes associated with each particular system identified and clearly defined?
While this is a straightforward “yes” or “no” question, in order to answer that question the IT auditor would need to look at an organization’s Business Impact Analysis and verify that the assets and security processes were indeed identified and clearly defined.
You will also notice that I have cross-referenced each of the steps to the appropriate sections within CobiT.
I hope the template ISO27002 Security Framework will be of assistance to you.
Kenneth
Hi Tariq.
Exquisitely detailed checklists are spread between ISO/IEC 27001 and ISO/IEC 27002.
Iso 27002 Controls Checklist
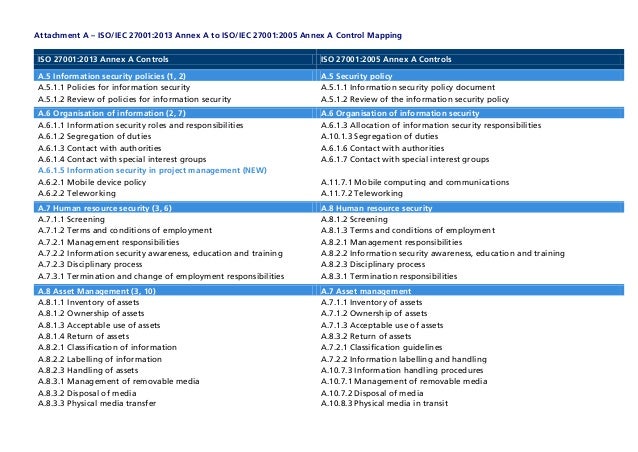
The new versions of ISO/IEC 27003 and 27004 will offer yet more wonderful advice on implementation and metrics, respectively, when released, hopefully this year.
Kind regards,
Gary
____________________________________________________

Dr Gary Hinson PhD MBA CISSP Cprof
CEO of IsecT Ltd., New Zealand www.isect.com
Passionate about information risk and security awareness, standards and metrics
www.NoticeBored.comwww.ISO27001security.comwww.SecurityMetametrics.com
--
Iso 27002 Detailed Controls
You received this message because you are subscribed to the ISO27k Forum.
To post a message to ISO27k Forum, send an email to iso27001...@googlegroups.com or online through groups.google.com
For more information about ISO27k, visit www.iso27001security.com
Please respect the Forum's rules at www.iso27001security.com/html/forum.html#TipsAndEtiquette
---
You received this message because you are subscribed to the Google Groups 'ISO 27001 security' group.
To unsubscribe from this group and stop receiving emails from it, send an email to iso27001...@googlegroups.com.
For more options, visit https://groups.google.com/d/optout.